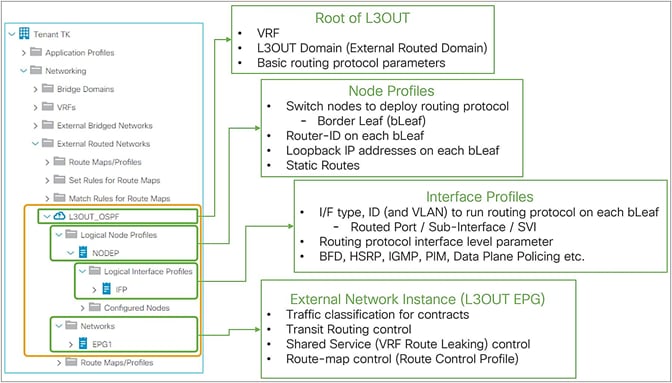
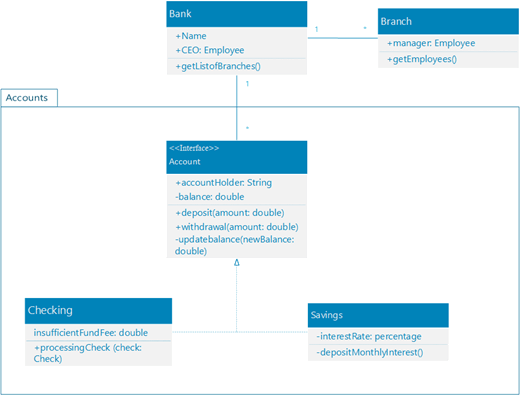
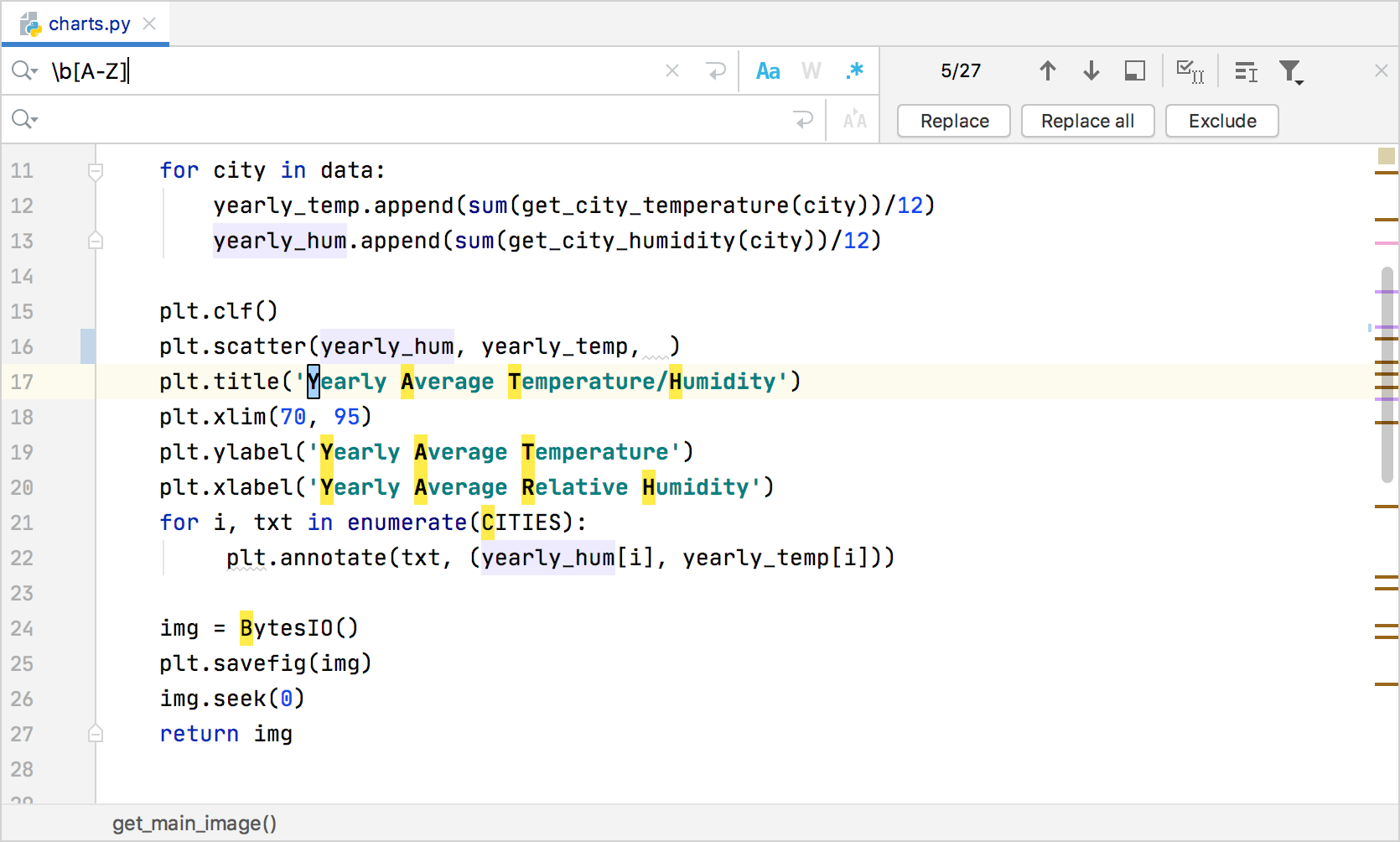
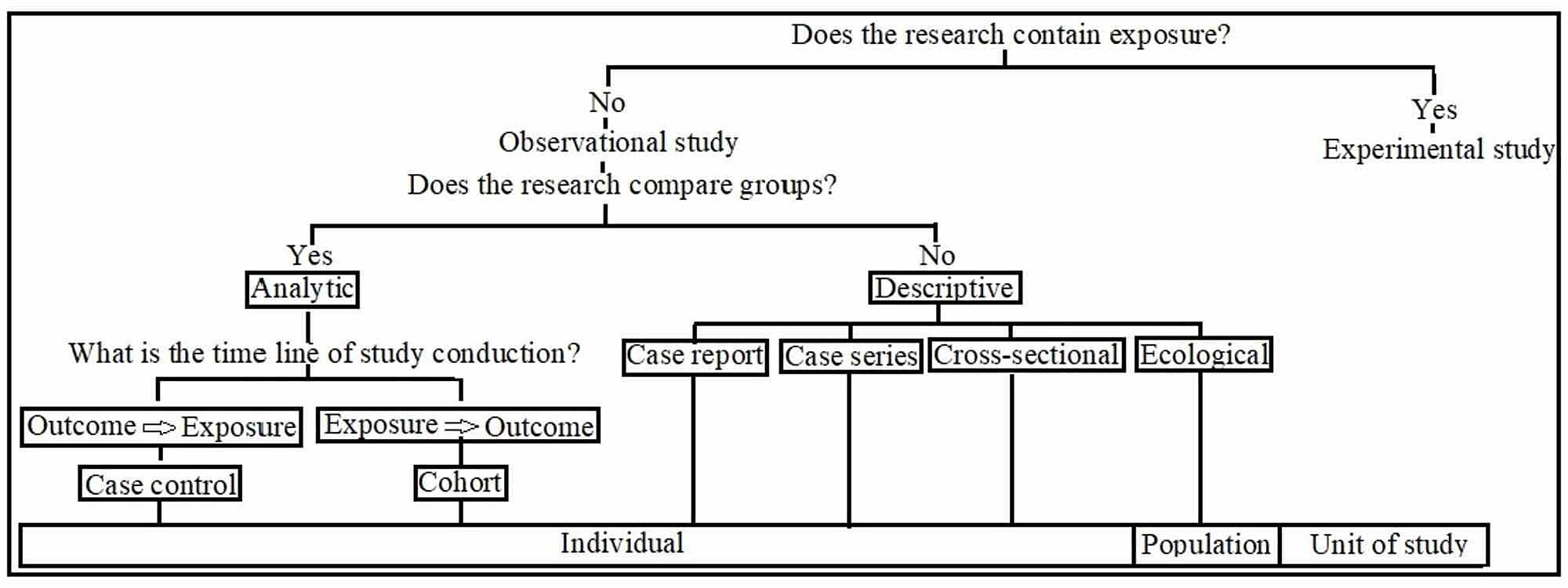
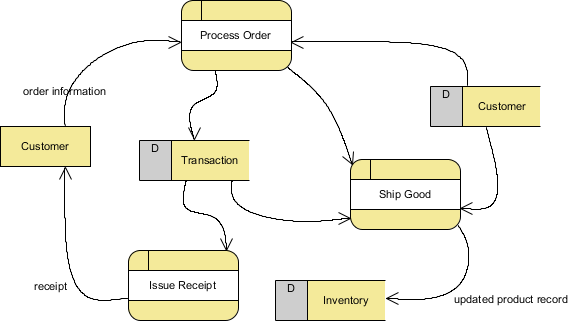
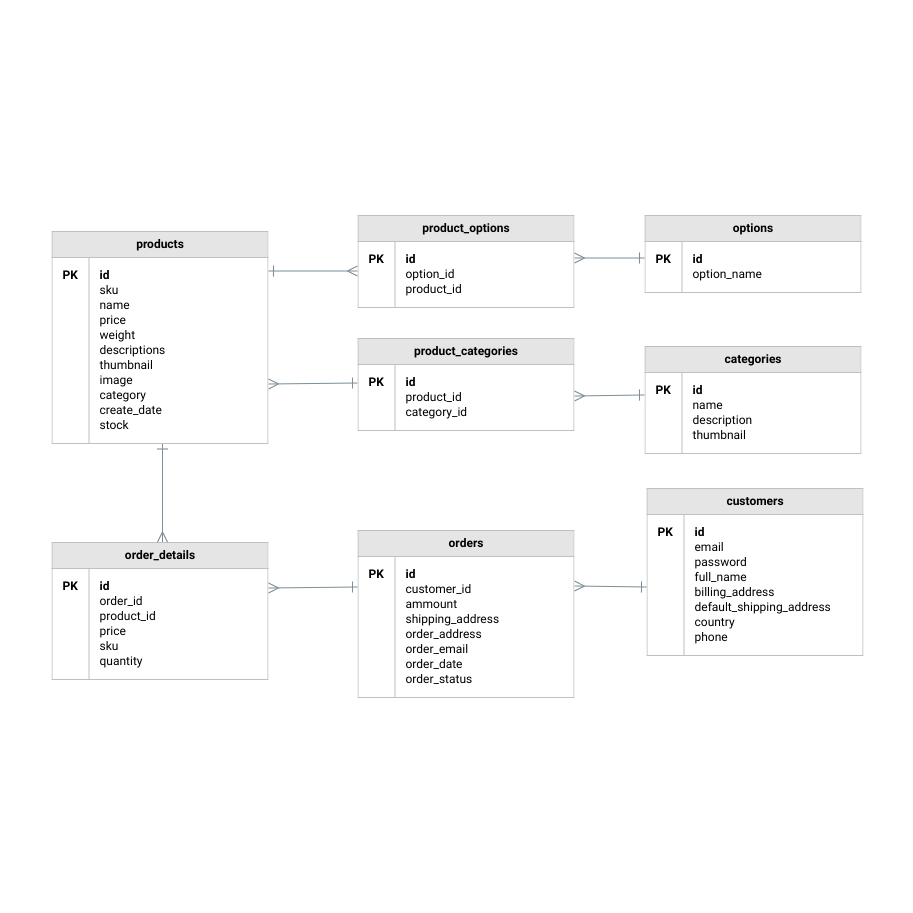
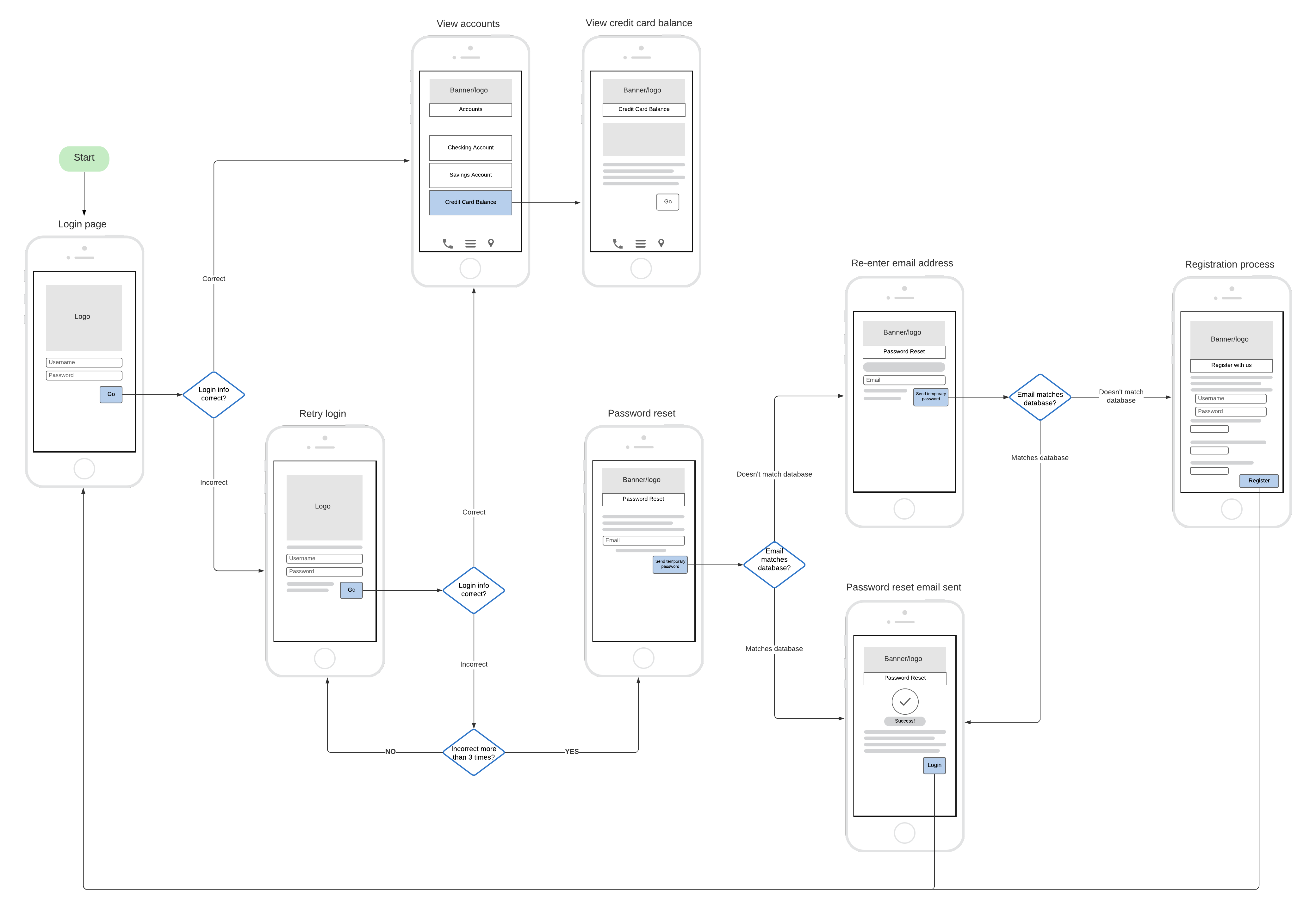
39 use the above diagram to match the case type
Write a program that takes the name of a file as a command line argument and prints out its file type extension. The extension is the sequence of characters following the last .. For example the file sun.gif has the extension gif. Hint: use split("\\."); recall that . is a regular expression meta-character, so you need to escape it. Reverse ... Administrators who want the Use Case Manager to evaluate rules must export their rules from QRadar using the generate-rules-script.sh utility. This utility generates an XML copy of the current QRadar rule set and can be automated so the administrators can import the information in to the QRadar Use Case Manager application to keep their rules ...
The challenge is to match to each row from T1 the row from T2 where the absolute difference between T2.val and T1.val is the lowest. In case of ties (multiple matching rows in T2), match the top row based on val ascending, ... The above diagrams are logical representations.
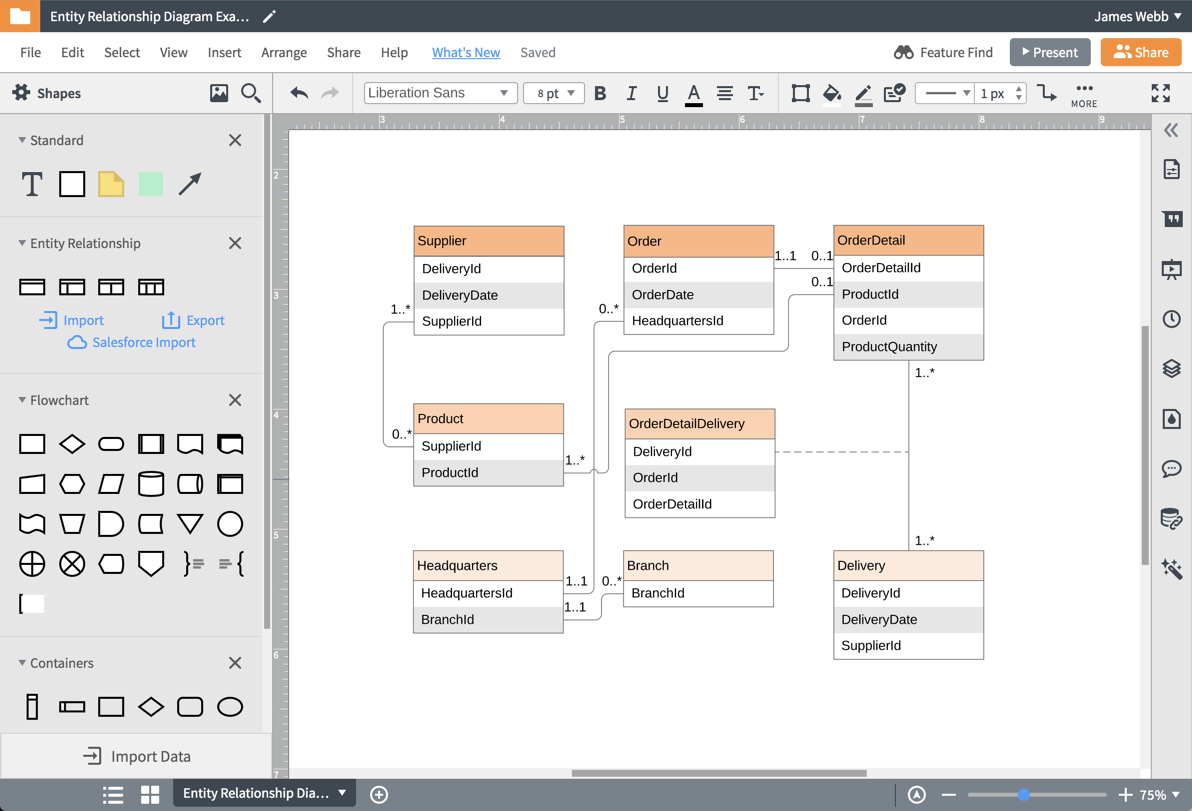
Use the above diagram to match the case type
THeorem: Double Integrals over Nonrectangular Regions. Suppose g(x, y) is the extension to the rectangle R of the function f(x, y) defined on the regions D and R as shown in Figure 15.2.1 inside R. Then g(x, y) is integrable and we define the double integral of f(x, y) over D by. ∬ D f(x, y)dA = ∬ R g(x, y)dA. Types of Networking Topologies. Two main types of network topologies in computer networks are 1) Physical topology 2) Logical topology. Physical topology: This type of network is an actual layout of the computer cables and other network devices. Logical topology: Logical topology gives insight's about network's physical design. NOTE Puppeteer can also be used to control the Chrome browser, but it works best with the version of Chromium it is bundled with. There is no guarantee it will work with any other version. Use executablePath or channel option with extreme caution.. If Google Chrome (rather than Chromium) is preferred, a Chrome Canary or Dev Channel build is suggested.. In puppeteer.launch([options]) above, any ...
Use the above diagram to match the case type. Then, proceed as in the ASA case, above. two sides and the area: See Given: Area and Two Sides, below. Find the included angle with sin A = 2 × area/(b c) Then, proceed as in the SAS case, above. ★ If a 90° angle is given, the Law of Sines and the Law of Cosines are overkill. Four Chambers of the Heart and Blood Circulation. The shape of the human heart is like an upside-down pear, weighing between 7-15 ounces, and is little larger than the size of the fist. It is located between the lungs, in the middle of the chest, behind and slightly to the left of the breast bone. The heart, one of the most significant organs ... Sometimes, some application is updated specifically to match the standard and style of a newer, more modern environment. In that case, support for backward compatibility is necessary. Backward compatibility testing ensures that all those who are using the older versions of a particular environment can use your software. 11. Above all, it is used to identify and address the areas of strengths and weaknesses. This consequently helps in better planning. This type of analytics importantly uses tools like MS Excel, MATLAB (MaTrix LABoratory), STATA, etc. Many learning systems use descriptive analytics for analytical reporting. They measure learner performance to ensure ...
Please refer to a Use case related topic in the foundation level guide "Use cases describe the "process flows" through a system based on its actual likely use" (actual likely use is nothing but the real-world use of the system). Use cases are useful for uncovering defects. Hence we can eliminate options (c ) and (d). Column patterns in derived column and aggregate. To add a column pattern in a derived column, aggregate, or window transformation, click on Add above the column list or the plus icon next to an existing derived column. Choose Add column pattern.. Use the expression builder to enter the match condition. Create a boolean expression that matches columns based on the name, type, stream, origin ... There are planning implications for the different locations, the type of data you want to monitor and protect, and the actions to be taken when a policy match occurs. Business processes planning for DLP. DLP policies can block prohibited activities, like inappropriate sharing of sensitive information via email. The above diagram shows how semantic analysis could happen. The flow of information happens bottom-up and all the children's attributes are computed before parents, as discussed above. Right-hand side nodes are sometimes annotated with subscript 1 to distinguish between children and parents.
There are three output files specified, and for the first two, no -map options are set, so ffmpeg will select streams for these two files automatically.. out1.mkv is a Matroska container file and accepts video, audio and subtitle streams, so ffmpeg will try to select one of each type. For video, it will select stream 0 from B.mp4, which has the highest resolution among all the input video streams. Which Fingers Go Where. Each finger rests on a particular key in the home row of the keyboard when not typing, in order to keep "grounded" and oriented at all times. The home keys (ASDF JKL; ) are outlined in yellow on the above diagram. The thumbs remain in the air, or very gently in contact with the keys below. The body uses feedback mechanisms to monitor and maintain our physiological activities. There are 2 types of feedback mechanisms - positive and negative. Positive feedback is like praising a person for a task they do. Negative feedback is like reprimanding a person. It discourages them from performing the said task. Cause-Effect Graph is a technique that starts with a set of requirements and determines the minimum possible test cases for maximum test coverage which reduces test execution time and cost. The goal is to reduce the total number of test cases, still achieving the desired application quality by covering the necessary test cases for maximum coverage.
The above format helps to be specific while setting up the event filter pattern for replay events (item 3 in the diagram). Instead of using the "replay-name": {[ "exists": true ]} pattern, it can ...
The magnetic field is an abstract entity that describes the influence of magnetic forces in a region. Magnetic field lines are a visual tool used to represent magnetic fields. They describe the direction of the magnetic force on a north monopole at any given position. Because monopoles are not found to exist in nature, we also discuss alternate means to describe the field lines in the sections ...
See Fig. 10-3 for the slope layering process and growth of sand dunes. There are five main types of sand dunes. These are the barchan, transverse, blowout, linear, and composite dunes. Although it is sometimes easier to see different dune types from the air, some deserts have only one predominant type. The barchan dune is a horseshoe-shaped ...
Interaction diagrams are used to explore and compare the use of sequence, collaborations, and timing diagrams. Interaction diagrams are used to capture the behavior of a system. It displays the dynamic structure of a system. Sequence diagrams are used to represent message flow from one object to another object.
Choose 2 answers. A. Reactivate the appropriate Shoe Style values after the field type changes. B. Select the "Choose only one value "checkbox on the pick list field. C. Back-up the Shoe Style values in existing records. D. Change the field type from a multi-select picklist field to a picklist field.
The combustion chamber is the space enclosed between the piston head and cylinder head when the piston is at the top dead centre position. It extends up to the upper compression ring of the piston. Exhaust and inlet valves open and close in the combustion chamber and the spark plug projects in it.. The design of the combustion chamber is of great importance for engine performance because the ...
This is separate to discovery auth. # configuration because discovery & scraping are two separate concerns in. # Prometheus. The discovery auth config is automatic if Prometheus runs inside. # the cluster. Otherwise, more config options have to be provided within the. # <kubernetes_sd_config>.
If we use Θ notation to represent time complexity of Insertion sort, we have to use two statements for best and worst cases: 1. The worst-case time complexity of Insertion Sort is Θ(n^2). 2. The best case time complexity of Insertion Sort is Θ(n). The Big O notation is useful when we only have an upper bound on the time complexity of an ...
In this case, the maximum bending moment can be evaluated as F1H* d. The second moment of area is πr4/4 (Since the cross section of the spreader beam is circular. As per class, s evaluated should not be greater than 0.6 * yield strength of the spreader beam material. Note that in the above evaluation, the weight of the beam is ignored.
The case for antigen testing is clear, in other words, and has been for some time. The tests have been used successfully in high-risk settings such as meat plants, and seven months ago a ...
In the latter case, product results were grouped together on the general results pages in what was called the Product OneBox ('Product OneBox'), either below or parallel to the advertisements appearing at the top or at the side of the page and above the general search results, as shown in the following annotated illustration, supplied by ...
NOTE Puppeteer can also be used to control the Chrome browser, but it works best with the version of Chromium it is bundled with. There is no guarantee it will work with any other version. Use executablePath or channel option with extreme caution.. If Google Chrome (rather than Chromium) is preferred, a Chrome Canary or Dev Channel build is suggested.. In puppeteer.launch([options]) above, any ...
Types of Networking Topologies. Two main types of network topologies in computer networks are 1) Physical topology 2) Logical topology. Physical topology: This type of network is an actual layout of the computer cables and other network devices. Logical topology: Logical topology gives insight's about network's physical design.
THeorem: Double Integrals over Nonrectangular Regions. Suppose g(x, y) is the extension to the rectangle R of the function f(x, y) defined on the regions D and R as shown in Figure 15.2.1 inside R. Then g(x, y) is integrable and we define the double integral of f(x, y) over D by. ∬ D f(x, y)dA = ∬ R g(x, y)dA.



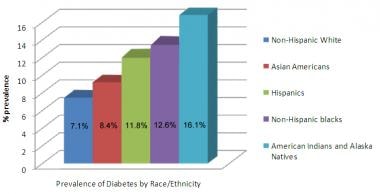


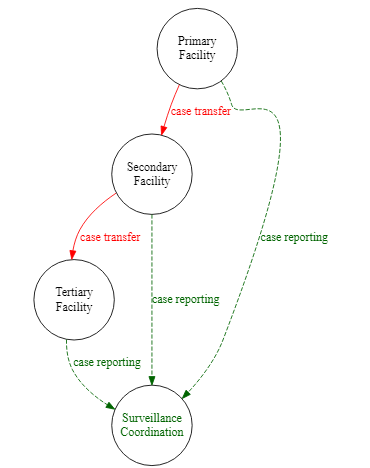

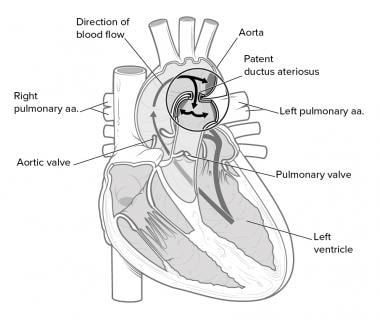











0 Response to "39 use the above diagram to match the case type"
Post a Comment